Below is a comprehensive list of my publications, organized by year. Click the titles to see full text (when available), authors, abstracts, BibTex citations, and any related images.
2022
(DAC) Apple vs EMA: Electromagnetic Side Channel Attacks on Apple CoreCrypto
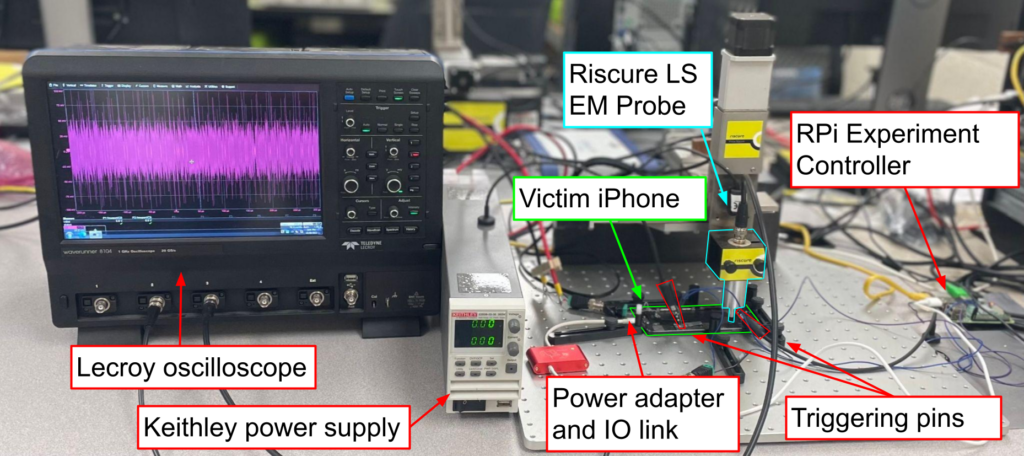
Gregor Haas, Aydin Aysu. Accepted to Design Automation Conference (DAC), San Francisco, USA, Jul 2022. Full text available here.
Abstract:
Cryptographic instruction set extensions are commonly used for ciphers which would otherwise face unacceptable side channel risks. A prominent example of such an extension is the ARMv8 Cryptographic Extension, or ARM CE for short, which defines dedicated instructions to securely accelerate AES. However, while these extensions may be resistant to traditional “digital” side channel attacks, they may still vulnerable to physical side channel attacks.
In this work, we demonstrate the first such attack on a standard ARM CE AES implementation. We specifically focus on the implementation used by Apple’s CoreCrypto library which we run on the Apple A10 Fusion SoC. To that end, we implement an optimized side channel acquisition infrastructure involving both custom iPhone software and accelerated analysis code. We find that an adversary which can observe 5-30 million known-ciphertext traces can reliably extract secret AES keys using electromagnetic (EM) radiation as a side channel. This corresponds to an encryption operation on less than half of a gigabyte of data, which could be acquired in less than 2 seconds on the iPhone 7 we examined. Our attack thus highlights the need for side channel defenses for real devices and production, industry-standard encryption software.
Bibtex:
@inproceedings{10.1145/3489517.3530437,
author = {Haas, Gregor and Aysu, Aydin},
title = {Apple vs. EMA: Electromagnetic Side Channel Attacks on Apple CoreCrypto},
year = {2022},
isbn = {9781450391429},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
url = {https://doi.org/10.1145/3489517.3530437},
doi = {10.1145/3489517.3530437},
booktitle = {Proceedings of the 59th ACM/IEEE Design Automation Conference},
pages = {247–252},
numpages = {6},
location = {San Francisco, California},
series = {DAC '22}
}2021
(IEEE HOST) iTimed: Cache Attacks on the Apple A10 SoC (Best Paper Nominee)
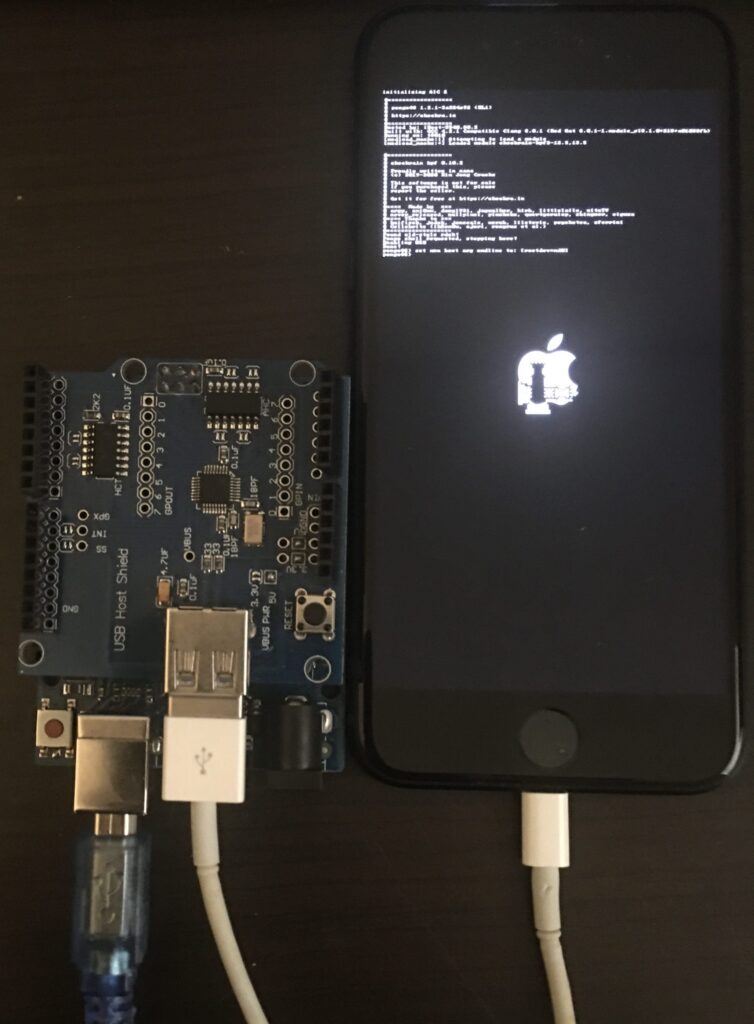
Gregor Haas, Seetal Potluri, Aydin Aysu. Accepted to IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington DC, USA, Dec 2021. Full text available here.
Abstract:
This paper proposes the first cache timing side-channel attack on one of Apple’s mobile devices. Utilizing a recent, permanent exploit named checkm8, we reverse-engineered Apple’s BootROM and created a powerful toolkit for running arbitrary hardware security experiments on Apple’s in-house designed ARM systems-on-a-chip (SoC). Using this toolkit, we then implement an access-driven cache timing attack (in the style of PRIME+PROBE) as a proof-of-concept illustrator.
The advanced hardware control enabled by our toolkit allowed us to reverse-engineer key microarchitectural details of the Apple A10 Fusion’s memory hierarchy. We find that the SoC employs a randomized cache-line replacement policy as well as a hardware-based L1 prefetcher. We propose statistical innovations which specifically account for these hardware structures and thus further the state-of-the-art in cache timing attacks. We find that our access-driven attack, at best, can reduce the security of OpenSSL AES-128 by 50 more bits than a straightforward adaptation of PRIME+PROBE, while requiring only half as many side channel measurement traces.
Bibtex:
@inproceedings{haas2021itimed,
title={iTimed: Cache attacks on the apple a10 fusion SoC},
author={Haas, Gregor and Potluri, Seetal and Aysu, Aydin},
booktitle={2021 IEEE International Symposium on Hardware Oriented Security and Trust (HOST)},
pages={80--90},
year={2021},
organization={IEEE}
}(MSc Thesis) Side Channel Attacks on Real-World Devices: A Case Study on Apple iPhones
Gregor Haas, advised by Aydin Aysu, Alessandra Scafuro, and William Enck. Submitted to NCSU as an MSc thesis. Full text available here.